Sunnic E-Trust
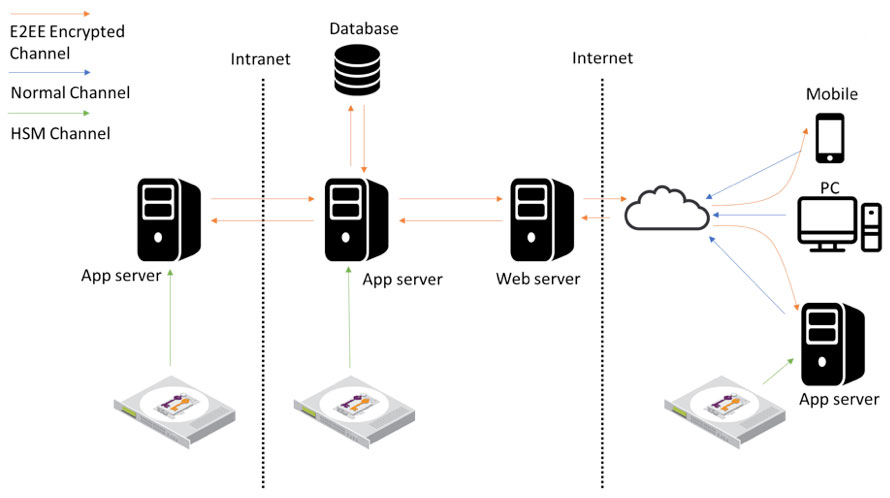
Application level encryption can be achieved using Sunnic E-Trust, which can be integrated with Federal Information Processing Standards (FIPS) Level-3 compliant HSMs. Sunnic E-Trust provides encryption for Data-At-Rest, as well as End-to-end encryption (E2EE), which ensures secure communication when data is transferred from one end to the other end, mitigating the effect of Man-in-the-middle attacks (MITM).
Encryption for Data-At-Rest
Sensitive data is encrypted at the application level before it is stored in a database. This prevents data stored in the database from being accessed by unauthorized individuals and prevents database administrators from having access to sensitive information. File level encryption is applied to data at rest such as text/file data in the database or any client file repository and will be secured by keys stored exclusively on either of the endpoints which is used for encrypting and decrypting.
End-to-end encryption (E2EE) for Data-In-Motion
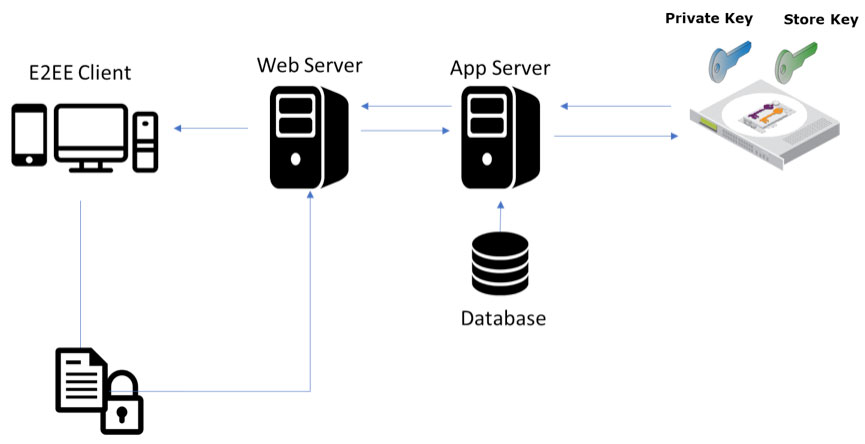
Application level encryption is applied and purposed to protect data in motion, so data stays encrypted from one point to another.
For example, the transfer of sensitive data between a bank and its partners can be secured by encryption at the point of entry, and before it is transmitted to the web servers. This increases overall security as both encryption and decryption of messages are done on the endpoints. Data that gets intercepted by a third-party during transmission be secure and unreadable to unwanted access.
End-to-end encryption (E2EE) for Authentication
E-Trust Guard ensures secure end-to end authentication where a security domain between the user’s device and the HSM is created. Within the domain, the password is encrypted at the user’s device and can only be decrypted for verification inside FIPS-certified HSM secure boundary. Thus, the password is not exposed, not even to the System administrator or HSM’s owner.